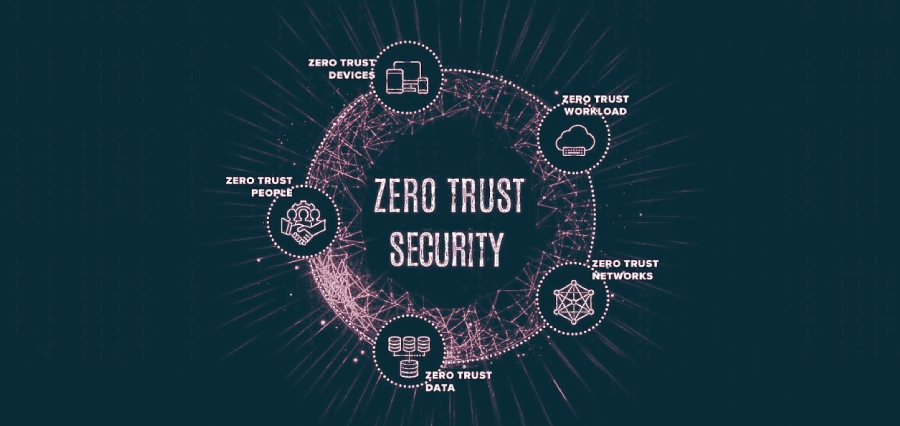
In the age of relentless cyber threats, the traditional castle-and-moat approach to cybersecurity is proving inadequate. As organizations grapple with increasingly sophisticated attacks, the concept of Zero Trust Security has emerged as a paradigm shift in safeguarding digital assets. In this exploration, we delve into the principles, applications, and benefits of Zero Trust Security.
The Foundation of Zero Trust: Trust No One, Verify Everything
Core Principles
Zero Trust Security operates on the fundamental principle of mistrust. Gone are the days of assuming trust within the corporate network. Instead, every user, device, and application is treated as potentially compromised, necessitating continuous verification.
Dynamic Identity Verification
Understand the role of dynamic identity verification in the Zero Trust model. Explore multi-factor authentication, continuous monitoring, and adaptive access controls as critical components in establishing and maintaining trustworthiness.
Micro-Segmentation: Fortifying the Digital Fortress
Beyond Perimeter Security
Micro-segmentation is a key strategy in the Zero Trust Security framework. Explore how organizations are moving beyond traditional perimeter security to compartmentalize their networks, reducing the attack surface and limiting lateral movement in case of a breach.
Use Cases and Benefits
Examine real-world use cases where micro-segmentation has proven effective, from protecting sensitive data in financial institutions to securing healthcare networks. Discover the benefits, including improved incident response and compliance adherence.
Continuous Monitoring and Analytics: Eyes on the Digital Horizon
Real-time Threat Intelligence
Zero Trust Security emphasizes continuous monitoring of network activities. Explore how real-time threat intelligence, user behavior analytics, and artificial intelligence contribute to identifying anomalies and potential security incidents.
The Role of Automation
Delve into the role of automation in continuous monitoring, enabling swift responses to security events. Understand how automated threat detection and response mechanisms align with the dynamic nature of the Zero Trust model.
Device Trustworthiness: From Endpoints to IoT
Securing Endpoints
In a Zero Trust environment, securing endpoints is paramount. Explore how organizations are implementing device trustworthiness assessments, ensuring that every device connecting to the network meets stringent security standards.
Challenges in IoT Security
With the proliferation of Internet of Things (IoT) devices, securing the expanding attack surface is a critical concern. Uncover the challenges in implementing Zero Trust for IoT and strategies to mitigate risks associated with these devices.
User-Centric Security: The Human Element
Context-Aware Access Controls
Zero Trust Security acknowledges the human element as a potential vulnerability. Learn how context-aware access controls ensure that users only access what is necessary for their roles, reducing the risk of unauthorized access.
Security Awareness Training
Explore the role of security awareness training in fostering a security-conscious culture. Understand how educating users about phishing threats, social engineering, and secure online practices contributes to the success of a Zero Trust Security model.
Overcoming Implementation Challenges: A Roadmap for Organizations
Start Small, Scale Gradually
Implementing Zero Trust Security can be a monumental task. Discover a roadmap for organizations, emphasizing the importance of starting small, identifying high-priority assets, and gradually expanding Zero Trust principles across the entire infrastructure.
Collaboration and Integration
Explore the importance of collaboration between IT and security teams. Understand how integration with existing security solutions, such as identity and access management tools, SIEM platforms, and firewalls, enhances the effectiveness of Zero Trust Security.
————————————————————————————
Author Introduction: Pritish Halder
Pritish Halder, a visionary in the realm of Information Technology, brings his expertise to unravel the complexities of cybersecurity. With a keen interest in emerging technologies, Pritish navigates the evolving landscape of IT security. Stay tuned for more insights as he continues to dissect topics that shape the future of digital resilience and security. Pritish is committed to empowering individuals and organizations with the knowledge needed to thrive in our ever-connected world.